checking the debug of the website today, I stumbled upon several strange records:
I don"t understand why a request to https://*.12306.cn is directed to my server
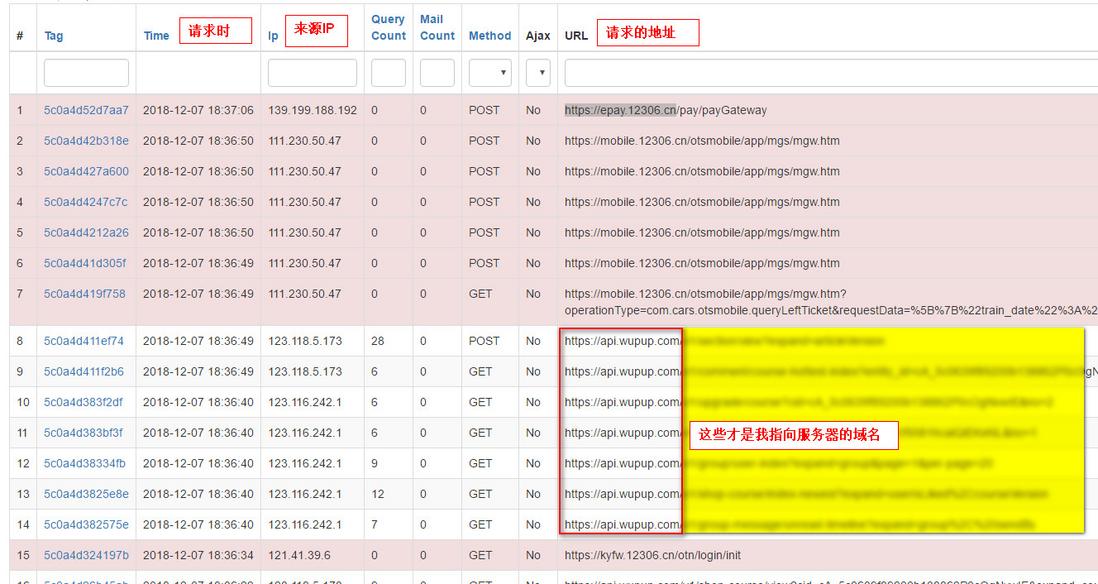
checking the debug of the website today, I stumbled upon several strange records:
I don"t understand why a request to https://*.12306.cn is directed to my server

https://epay.12306.cn/pay/payGateway at 2018-12-07 06:37:06 pm by 139.199.188.192 https://kyfw.12306.cn/otn/login/init at 2018-12-07 06:36:34 pm by 121.41.39.6 https://mobile.12306.cn/otsmobile/app/mgs/mgw.htm?operationType=com.cars.otsmobile.queryLeftTicket&requestData=%5B%7B%22train_date%22%3A%2220181217%22%2C%22purpose_codes%22%3A%2200%22%2C%22from_station%22%3A%22PIJ%22%2C%22to_station%22%3A%22POJ%22%2C%22station_train_code%22%3A%22%22%2C%22start_time_begin%22%3A%220000 % 22%2C%22start_time_end%22%3A%222400%22%2C%22train_headers%22%3A%22QB%23%22%2C%22train_flag%22%3A%22%22%2C%22seat_type%22%3A%22%22%2C%22seatBack_Type%22%3A%22%22%2C%22ticket_num%22%3A%22%22%2C%22dfpStr%22%3A%22%22%2C%22baseDTO%22%3A%7B%22check_code%22%3A % 227d6a7259915ae11894d2afae8b3cb8a9% 22% 2C% 22deviceroomno% 22% 3A% 2261af7de9dbacd2b6% 22% 2C% 22mobileroomno% 22% 3A% 22% 22% 2C% 22% 2C% 22% timekeeper% 22% 3A% 2220181207183649% 22% 2C% 22username% 22% 3A% 22% 22% 2C% 22versionremote no% 22% 3A% 221.9% 227D% 7D% 5D% 5D examples signalling = at-2018-12-06:36:49 111.230.47 change the local hosts . You can change the hosts of your local computer to point baidu.com to your ip. You are visiting baidu.com to have a look.
it is estimated that this client's local hosts or a route in the middle has been tampered with, pointing 12306.cn to you.
I check the server log, and the situation is the same as yours. Just leave it alone?
I have one, too. What should I do?
Hello, boss. I'd like to know how to deal with it in the end. In the same situation on my side, looking at the log of nginx, I found that there is a steady stream of requests for otsmobile/app/mgs/mgw.htm?operationType=com.... every day. The status is 301.
can only infer that someone took advantage of the server traffic and then forwarded the request (otsmobile/app/mgs) to 12306 (presumably) to swipe the ticket.
but I checked nginx and didn't find any changes to the configuration file.